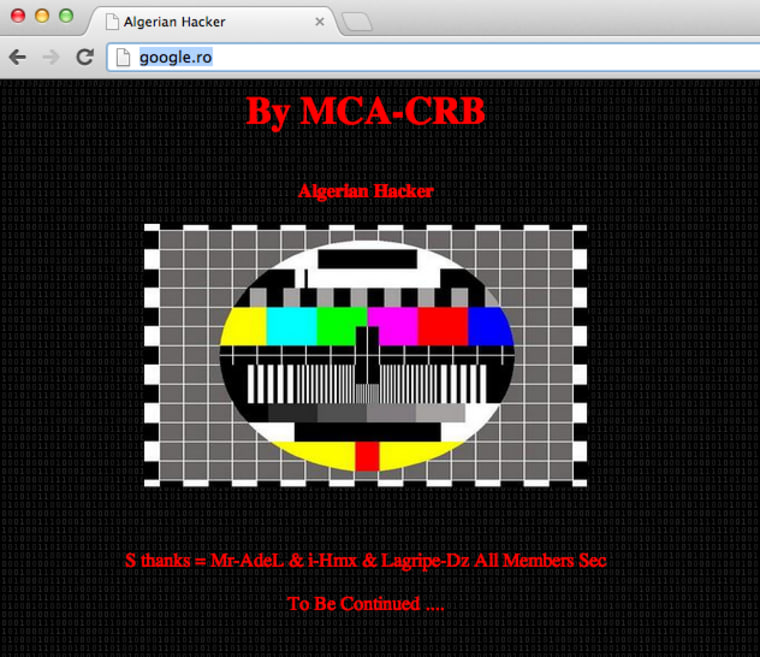
There were reports this past week that Google's Romanian and Pakistani portals, Google.ro and Google.com.pk, had been hacked. But if you're worried about the security of your Google account info, you can relax: By most standards, this was nothing like a "real" hack. But it does show off another way that hackers can mess with the system.
It's true that people throughout the world found themselves looking not at the familiar search engine page but at a message from a proud hacker, it wasn't Google that got hacked. What happened was something called "DNS cache poisoning." While it sounds serious, it's not a security breach — more like a bad rumor going around the Internet.
DNS, or the domain name system, is how the Internet keeps track of itself. With billions of websites corresponding to billions of IP (Internet protocol) addresses, many of which are constantly shifting, keeping track of which site goes with which address is an incredibly complicated job.
Furthermore, because authorities and methods differ between countries and regions, there are many DNS servers with conflicting information. Sometimes one mistake can be amplified and experienced around the world.
To help you visualize DNS, imagine you're on a long street lined with shops. You know what shop you want, but you don't actually know which door to enter, and not only that, but they keep rearranging the signs. To get to your destination, you have to ask the helpful people in the street, all of whom are more or less familiar with which door is which.
You tell one of these guides: "I'm going to Google." Chances are he knows, and will reply, "It's the red door with the white sign." If he isn't sure, he asks his neighbor, who might be a little more up to date. And if that neighbor doesn't know, he'll ask his neighbor, and so on. Usually these guys are pretty knowledgeable, and every fresh query updates their outdated information.
But because this system is based on trust, false information can still be spread, either intentionally or not. Someone might start a rumor that Google's door was blue with a green sign, hoping to drive traffic to this other door instead. The majority of guides knows not to trust such random rumors, but everyone makes mistakes. So sometimes that information will travel all the way up and down the line until someone points out that the blue door does not in fact go to Google.
Starting a "rumor" like that in the domain name system is called poisoning or spoofing the DNS. It begins when a normally reliable DNS server reports incorrect domain data. That information may simply be a mistake, as with a Google outage earlier this month stemming from an error in Indonesia.
Or it may be deliberate, as the case appears to be this time: Someone got the servers managing the ".ro" Romanian domain to announce not just the wrong IP address for Google.ro, but a specific wrong IP of that person's choosing, pointing to their own webpage touting the "hack." Similarly, in Pakistan, the records for nearly 300 sites, including Google's and Apple's, were deliberately rewritten.
The result: Millions of people who tried to use Google were steered to some hacker's site (which fortunately did not not host any malware or other objectionable content). But it's important to note that Google itself was untouched. No matter how many people are directed to the wrong "door," the data and accounts that Google comprises are as safe as they've ever been.
In contrast, a "real" hack would be if someone actually gained access to Google's data — its own code, or user names, emails and passwords, that sort of thing. It's the difference between burglarizing a store and giving out bad directions to the store. That said, a DNS redirect around Google means trouble for the company, not to mention for those who manage the Romanian and Pakistani DNS servers. Any security breach would have been on their side, so they've got more to worry about.
There's not much anyone at home can do to "protect" against this kind of Internet fraud, except make sure their computer's malware protection is up to date. DNS spoofing has to be resolved on a higher level, and the solution takes time to propagate. If you encounter a page that seems to be broken or defaced, don't linger or click around. Leave the site and give the system administrators time to sort it out before you go back. Chances are, the admins are already on the case — they would have been among the first to notice that their own site was broken, after all.
Devin Coldewey is a contributing writer for NBC News Digital. His personal website is coldewey.cc.